Intro and how to read this article
On August 30th I passed the OSCP exam.
Please, before jumping into reading this article, let me explain how it is structured. My aim is to provide a clear overview of the whole OSCP journey. Therefore, I divided it into two bigger sections:
- The first one is about an-high level overview of the journey itself. So I tell you my background, what the OSCP is, what is not. I also tell you in details how I see the OSCP
- Then, what was my approach before/during/after the PWK labs access, how I approached the targets during the training and during the exam too, how I took notes. And finally, even how I reported all the findings in the exam.
You can find most of the resources in my GitHub repo, I highly advise you to check it out.
The OSCP bundle I got
My company paid for me the Offensive Security Academy bundle, which includes:
- 90 days of access to the PWK labs.
- A weekly online meeting with all the class during the 90 days of lab access.
- 1:1 call with the instructors.
Just to clarify, 2 instructors and 30/40 students formed the Offensive Security Academy. They divide the latter into two classes.
Background
At the time of writing, I am working in the IT industry since 2019. Before then, I was in the Army. My highest education is the High School Diploma in Information Technology, now I am studying at the University of Milan for the Computer Systems and Networks Security.
Once I landed my first civilian job, I got a role in an Italian Holding as Sysadmin/Technician. During that time, I read a lot of InfoSec relevant books; I watched a lot of videos about cybersecurity, and then I started studying for the CompTIA Security+, for which I wrote an article that you can find here. After the Sec+, I’ve started playing on TryHackMe for some months, then because of workload I had to cut it off.
My technical background is not the best at all, but not even the worst. I have fundamental knowledge in systems, networks and programming. I enjoy a lot programming in Python. This certainly helped me a lot.
What is and what is not OSCP
The Offensive Security Certified Professional is the title you earn by passing the OSCP challenge (the exam). This certification is an entry-level step for the penetration testing universe, not for general IT, neither for advanced penetration testing. This means that before you can jump on it, you should have a solid fundamental knowledge of systems and networks.
So, I am speaking to you ECPPT holders.. You can’t be surprised if you don’t get 10k slides for the OSCP, this is a different certification with a different objective. And, I am speaking to you too EJPT holders, this is a penetration testing entry-level, it means that you should already have fundamental knowledge :)
BUT, I love you all, peace.
Let’s move on to discover what really is the OSCP aim from my point of view.
OSCP’s main objective (imho)
It aims to give you a strong forma mentis that I hardly see in people. It helps you develop the mindset you need to overcome obstacles that you will always find in the everyday life, not only in your security assessments. The course materials give you only an introduction to the pentesting universe, so you have to do your own researches to progress in the PWK labs and to pass the exam. This will craft and harden your critical thinking and researching skill, which are not negligible traits.
To be more precise, I think it tests the candidate in the following areas:
- Intelligence Gathering
- Stress management
- Time management
- Communication
Meanwhile, the OSCP does not take you by hand and they do not structure it in a way to test you on a real pentesting assessment. It goes beyond it. This must be clear in your mind.
The four elements!

Dear reader, this is the most important part of the entire article. In my opinion, this is the OSCP’s essence.
I hope you understand all these four elements and I would like if you assume them not only for the exam itself, but for everything you are and you will be doing. Honestly, I think they are the foundations for the mindset taught by OSCP.
Information Gathering
OSCP forces you to learn how to research information. This element is the most important, because without this ability you can forget to pass the exam.
Seriously, learn how to gather information from the target and about the target. Where from and about stand for two different locations and the target can gain different shapes. Wait for the My TTPs section to learn more about it.
Stress management
Another important step is the stress management. Just to clarify, with stress I am referring to mental and body fatigue, to the sense of anxiety that pervades you, to everything that puts you in a bad mood or in a very high alert state.
Train yourself to manage it. If you are not used to the stress and you can’t handle it, I highly suggest that you learn it right now. How? Start doing the boxes, giving you a maximum time. In the meantime, practice some breathe exercises and drink water. Look on the Internet and find what fits you the most. What is important is that you arrive at the exam that you know how you handle the stress, how your brain and your body react to it.
Even if you have 23h45’ for the exam after 10/12 hours, the most of your energies will be gone. So it’s fundamental that you know how to handle it.
Time management
The third bastion is the time management. Maybe you are a beast and after 6 hours you have pwned all the boxes, I’m happy for you. But the OSCP is not a race between the students. You must learn how to manage your time. Again, you have to do a lot of practice. Start asap to get used to the timer and, during the exam, respect the timers you will set!
This helps you to maintain enough focus on all the boxes and prevents you to hopping from one box to another, and another just after a few minutes.
I show you in greater details how I managed my time along the whole article.
Communication
Last but not least is the ability to communicate. After your practice exam, you must write a report of what you have done and send it to OffSec.
I don’t their internal judgement metrics, but I am pretty sure that the better you write, the fewer probabilities to be rejected will there be. Start from now to do a brief report of each box you pwn. Get used to take screenshots, highlight on them the important part, clearly write the process you did to root the target. This will extremely help you during your exam report.
What I did before/during/after the PWK course
Before the PWK beginning
Four weeks before the beginning, I joined the OffSec Proving Grounds Practice platform, where I started doing the easy and medium boxes. In the meantime, I looked every day for exam reviews and suggestions on the web (blog, YouTube, Reddit, etc.). For the first three weeks, I avoided automation at all and I tried to go manual mode with everything. This helped me to better understand what happens under the curtains. Then, I started using nmapAutomator for the enumeration part.
During the PWK course
Once OffSec opened the doors, I checked the PDF by reading the sections I found more interesting. This took me a week. Then I started digging in the PWK labs by following the official learning path. After a few machines, I got bored (because of the way I am, not because of the learning path), so I picked up the targets based on my feelings.
My mentality was to go first on the stand-alone machines (The official forum will be helpful for this), and then move on the others.
Initially, I focused on finding the flags. Then I switched my focus to what the target was trying to teach me. Start doing it from the beginning.
After the PWK ending
Actually, Offensive Security gifts us with a lab extension of 30 days, but I was happy enough with them so I just switched to my OSPG Practice.
I really started crushing the Practice boxes. Fortunately, thanks to an Italian Discord server, I found an awesome group to train with. This let me grow really fast.
TL;DR
Try to organize at the best your studies during the pre/during/post course periods, do not just go through the whole course without any schedule.
How to approach boxes in the PWK labs
It all depends on your life, skills and the bundle you get.
You may be a human being with a lot of free time or someone who is working full time, studying at the university, studying for the certifications and trying to having enough social life.
If you have a lot of free time, my suggestions are:
- Look at the PWK labs like a real enterprise network. This is not directly helpful for the exam, but it will help you sharp your reconnaissance skill and critical thinking imho.
- Do all the machines.
- Prefer the manual exploitation way, but do not avoid every time the automatisms.
- Look at the Note taking and reporting.
If you don’t have a lot of free time (I feel you), my suggestions are:
- Focus first on the standalone boxes, use the forum to learn which are standalone and which not.
- From the first day, set a maximum time to spend on a single box. At the beginning, I spent 10/12 hours of actual work on a machine, then I reduced this time to 4 hours, then to 2 hours. Try it and find a time that fits your routine. The rule is to not spend too much time on a box, I always preferred to ask for help to learn a new stuff.
You don’t know what you don’t know.
- Prefer the manual exploitation way, but do not avoid every time the automatisms.
- Look at the Note taking and reporting
Least but not last, the bundle you get matters. With the 30 days pack, go straight to the standalone boxes. Otherwise, if you have time, keep calm and enjoy the labs.
TL;DR
Uhm… I don’t know how I can resume the above part, just read it all.
How to approach boxes in OSPG Practice
Down here the environment is different, and one thing that I feel everyone who is preparing the OSCP on OSPG Practice needs is to understand how the box rating system is.
In OSPGP, we can find 3 categories based on the general difficulty:
Warm up (Easy)
Get to work (Intermediate)
Try harder (Hard)
So, in each category we have a set of easy, intermediate or hard machines. Remember, this is the rating given by Offensive Security.
At the time of writing, I found the major pattern that OffSec follows to rate their PG Practice machines. This pattern is because of the step needed to root.
| Number of EoP | OffSec Rating |
|---|---|
| 0 | Easy |
| 1 | Intermediate |
| 2 or more | Hard |
This does not apply everytime but that’s regular enough.
A part from the OffSec rating that could be misleading, we have the Community rating. You just need to move your cursor on the machine’s name to find it. As you can see, in the screenshot I was looking at Hawat. Based on OffSec rating, this is an Easy box, but based on the Community rating, this is Very Hard. In fact, in this case, Hawat does not need any EoP to get root, but to process to get there is tricky for most students.
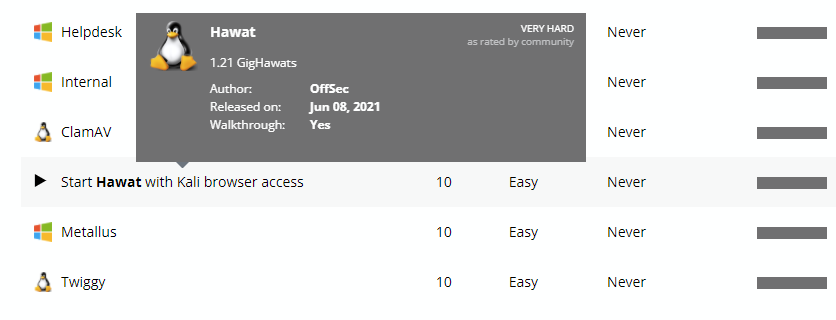
By knowing this, I would suggest that you look at both ratings before starting a box. If you are at the beginning, maybe skip the hardest boxes so you can enjoy them later.
Once you have understood this, my biggest suggestion is to tackle down the more boxes you can, from the easiest to the hardest. Meanwhile, stay away from some of the hard as they are very hard and way out of scope for the OSCP exam, but still interesting to work on once you get your certification ;)
When you are getting closer to your exam (2/3 weeks prior to the big date), focus only on the boxes rated Intermediate/Hard, both from OffSec and the community.
Then, even here follow the tips under the note taking and reporting to report everything.
TL;DR
Be conscious about the PG practice environment.
Notes, notes, notes.
My TTPs

I wrote some checklists to support, you can find them on my GitHub repo, again.
Firstly, consider to interact with the target first without having it in the hosts file, then add it to the file and look for differences.
At the beginning, I launch Inscursore against the target. In the meantime, I enjoy the moment and wait for the results. I avoid working on the target until I got an overview about it, because I influence too much myself. Once Incursore finished its raid, by looking at the results, I aim to understand:
- Which OS is running
- Which is the target’s purpose: DC, DNS, MAIL server, DHCP server, workstation?
- How large is the attack surface
Then, I enumerate the services running at each port. In this phase, I avoid going deeply into one service. Instead, I prefer to follow the “onion” logic and look at the target as a layered element. For example, let’s assume that the target is running FTP on 21, HTTP on 8081 and SMB on 445. I log into it and I find a lot of files and folders. I only give a brief look at these findings, then I switch to the SMB service, a brief look, then a brief look on the HTTP, and so on.
After this general overview, I start dissecting each service, if after 20-40 minutes I have not find anything, I switch on the next service and so on. Bear in mind that if a service seems to be useless, it could turn out to be the key for the kingdom after you find a clue on another one.
This man explains it way better than me, you should watch this video https://www.youtube.com/watch?v=9UFU6Y3c1qM.
Moreover, I try to gather as much information as possible at each step. So, every time I get a step ahead on pwning the target, I look around and I try to become more aware of the whole context. This helps me to understand how to better move to achieve my goals. Then I like to see the IG process under two sub-categories:
- The gathering from the target: I intend to gather all the useful information that the target has to offer from itself.
- The gathering about the target: I mean to gather all the useful information that I can find about the target from other resources and point of views.
At the beginning of the OSCP journey, my approach was a messy. Then, after spending a lot of times on the boxes, I found a general pattern that works for me every time. Go and find yours.
TL;DR
My biggest advice here is to not deep dive immediately on a service, take your time to get a general overview about the target and its services, then go deeper.
You need to see the big picture to connect the dots.
Do not spend too much time if the service did not take you anywhere. Maybe it could be useful later.
Contextual awareness is key, the enumeration is the mean to it. Gather information from the target and about it, change your point of view, cross-reference the information.
Note taking and reporting
This section is very important as if you learn how to take notes and report them, you’ll be very advantaged.
Note taking and reporting during the training
Do not waste too much time looking for the silver bullet of note taking: it does not exist. Invest some time looking for some of them, then pick a set of softwares that inspires you. Try to use for a while one software, then switch to another one. After 3/4 weeks, you should have a clear overview of what your tastes are and what the softwares offer you. Make your choice and start using that software in and out.
For example, I tried to use Cherry Tree, Joplin, Notion and Obsidian. I felt in love with Obsidian. I added the template that I created on my GitHub repo if you need some inspiration.
Now, take notes and screenshots of every success and failure, comment them on your notes. Then try to write a brief report for each machine. If during the note-taking process, you follow something like my template, once you pwn the box, you will already have a pseudo report to look at. This will save you a lot of time.
Another suggestion that I would to give you is to create a template for the BOF box. This 25 points machine should be the easiest one in your exam, and it could be the fastest one too, if you know how to do it. What you can do to lower the time is to prepare a template where you will just insert the minimal information and screenshots. To better understand what I am saying, look at this template that I posted on my GitHub repo. I wrote it by following this TryHackMe room.
The exam report
Obsidian generates .md files, I know that there are some scripts that will autogenerate a report from these .md files, but I preferred to write my report on Microsoft Office Word using the official Offensive Security OSCP report template, that I changed a bit. You can find my final template report here.
TL;DR
Start taking notes asap.
Try to write some simple report about each pwned box.
Create templates you’ll easily fill up while working on the box.
Exam
Sanboxing the work keeps the issues away
I found that the clearer my desktops are, the better I work. To keep a kind of order on my computer, I used the workspaces. I dedicated the first workspace for the VPN connection and the Exam web portal. Then I used a unique workspace for each target.
How I crushed the targets
Once I finished the identification process, I launched Incursore (My automation enumeration tool) against the 4 boxes from their respective workspace, then I started with the BOF. I took a lot of screenshot using Flameshot and I highlighted the most important information on the fly (You can do it with Flameshot, it’s awesome, you should play a bit with it.). I put everything in my pre-made BOF template. Once I finished the BOF, I took a quick break then I checked that my notes and screenshot were ok. Only after it, I started working on the other 25 points machine.
Keep track of your time
The most important thing that I want to say about it is to prepare yourself before the exam and not at the beginning of it.
If you don’t know yet, the practical part of the exam lasts 23h45'. It could seem to be a very little time for you at the moment, but believe me that if you are going to prepare well, you won’t need all these hours at the exam. Take your time to find how to work with timers and how to handle the breaks. Some days before the exam, I prepared a set of timers on my computer.
And take some rest, seriously, do not rush through it without any break.
- The Box hop was the maximum time I gave myself to work on a box before jumping on another one
- The Reduced box hop was the maximum time I set to work on a box in the case that the 2 hrs expired but I felt that I was near to root it
- The Box bonus time was the same as the Reduced box hop but smaller
- The Turning point was to remind me that 11h45' were passed
- The 16 hrs gone is straight forward
- The breaks timer were used during a box timer if I needed a break, after getting a foothold/EoP or before switching on another target
I finished way earlier, what should I do?
As I’ve already said, if you are well prepared you are going to finish earlier. Even if you have not got 5 out of 5 but you are confident to have enough points, consider what I am going to say down here.
My suggestion is to take a longer break, do some PT (Physical Training), watch some TVs, do whatever you like, maybe go to sleep for some hours, just don’t waste the whole remaining time.
Once you come back on the keyboard, start testing again the boxes by using your notes. So you will check your notes, your screenshots and your proofs, and you will be still in time to fix errors and missing parts. Another task you should consider is to check the proofs submitted on the web portal that OffSec gives you at the beginning of the exam.
Feel free to skip these steps, but you should value them. Remember that if something important is missing you will not get useful points for passing the exam.
TL;DR
Have a clean and ordered environment both on your computer and in the room you are working in.
Keep tracks of the time passed, the time for each box and for each break. Do not waste it.
Rest, rest, rest.
Finished earlier? Relax, then use the remaining time to check the consistency of your notes and findings.
For the numbers lovers
I am sorry but I am not one of them, I prefer getting my hands dirty.
I know that I have rooted 22 boxes in the PWK labs and 35 boxes in Proving Ground Practice. Nope, I have not cleared out a thousand boxes on HTB, VHL and so on. I have to admit that I have done some stuff on TryHackMe, but it was a year before the OSCP course.
Other than that, during the exam, I rooted 4 boxes out of 5 under 9h30'. And… I wasted most of my remaining time on the 5th box, blame on me.
Community
The lone wolf ideology is rad, but if you find a herd, it is way better.
No matter if you are doing the OffSec Academy or not, create a group of study to do this journey together. You will learn more and faster than going alone in the dark.
RTFM
Read The Fuc*ing Manual.
Seriously, take your time to read the official support documentation provided by Offensive Security. They did a great job with it.
Read, understand, read and understand. Period.
You will find:
- How the exam is structured
- What to do in case on network issues
- What do do in case of issues during the exam
- How to report the findings during the exam
- How to submit your report
- What you can and what you cannot do during your exam
- and a lot of other very useful information.
TL;DR
RTFM, RTFM, RTFM.
Final thoughts
I tried to write something different from the usual OSCP reviews, because I always find that something really important is missing. It is not how the exam is structured, how good/bad the PDF is, how the labs are, and so on. Honestly, I think that a lot of reviewers, even if they write great reviews, still miss the biggest point: what is the real OSCP’s essence. Given that, I hope I filled the gap an inch more with this one.
Final tip: Do not neglect who loves you (lovers, family, friends and animals). If you feel you are not being nice to them because of the OSCP, stop and reflect on how you can better organize yourself. If you feel you are under too much stress, there is nothing bad about relaxing a bit. Take it easy, mate.
Be just yourself, do not rush it, embrace simplicity, enjoy the journey.
Stay safe out there.
Thanks for taking the time to read this.